New technologies are the way forward in today's business landscape. To see this, look no further than the recent trend towards hybrid or remote working. In 2021,
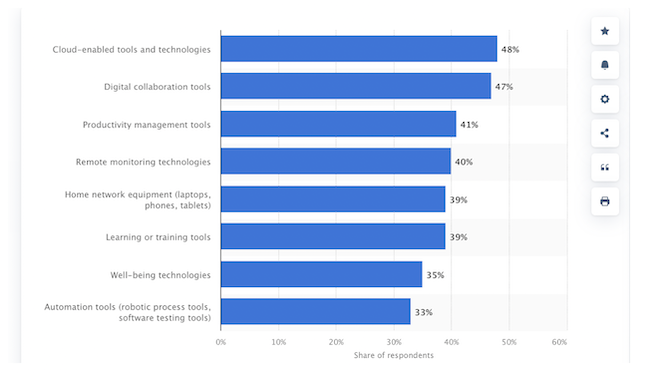
48% of businesses invested in cloud-based solutions, and nearly as many invested in teamwork and productivity management tools. These new technologies range from simple communication tools to project management software that promote trust in remote teams.
One of the most popular and versatile technologies being adopted by companies at the moment is vVoice over iInternet pProtocol systems, or VoIP systems.
What are VoIP systems?
VoIP is a cloud-based alternative to traditional calling methods like landlines. It involves communication between devices using an IP address. Most people have used them in the form of Zoom or Microsoft Teams.
VoIP systems work by forming a connection over an IP address between devices and sending voice data between these devices. It uses an encryption protocol in which voice data is broken down into smaller 'packets,', sent along the connection, and reconfigured properly at the receiving end.
Source
The major benefit of VoIP over traditional communications is that they can be easily scaled to suit an individual business' needs. These systems also rely far less on on-site hardware and constant physical maintenance than landlines.
They are a key part of many companies' strategies for
successful business communication.
VoIP security
One of the big concerns that consumers tend to have with VoIP systems is their security. Businesses are typically familiar with landlines, including the potential pitfalls and security risks, because they've been the dominant method of business communications for years.
Now that VoIP is surging in popularity, there have inevitably been questions over its security. Keeping your business communications secure is vital to maintaining
a positive team culture and earning consumer trust.
Your team should be aware of potential security risks and what measures they can take. Some examples include:
Understanding what data protection rules they must follow. Understanding basic VoIP skills, like how to invite someone to a meeting and grant them access. Understanding any company policies on VoIP use and data, including retrieval methods like elasticsearch documentation.
Let's be clear that VoIP is a secure and quick way of communicating. Many of the concerns over its security come from the fact that it's largely decentralized and most services host communications over their own servers. This lack of control can make business owners nervous about adopting VoIP.
VoIP systems are generally more secure than landlines for two reasons:
1) Higher security capacity: landline hacking relies on physically tapping into the connection between devices ('wiretapping'), so monitoring the security of these systems is difficult and expensive. VoIP systems come with lots of potential security protocols and add-ons.
2) Encryption: landline hackers will be able to hear everything being said in a given conversation. With VoIP, your conversation is encrypted during transmission and only decipherable by the sender and receiver.
5 VoIP security risks you should know (and how to resolve them)
Security breaches and data leaks are potentially very serious for a business. Loss of data on staff and customers can result in a loss of trust and a decrease in brand popularity and sales.
Source
Thankfully, by understanding some of the most common VoIP security risks, you can preempt them and manage them quickly and effectively when they arise. These are some of the major security risks that you may face when adopting VoIP, as well as how to go about resolving them.
1. Call tampering
Call tampering is not the most serious security risk mentioned here, but it's certainly frustrating to businesses and may limit the quality of their customer interactions. This is particularly true for businesses with a strong emphasis on customer/client calling.
Call tampering occurs when a hacker deliberately inserts large amounts of data into the call connection or delays the transmission of a call. This can result in long periods of silence or a poor connection with lots of background noise. This can make it difficult for the recipient of the call to focus or to hear important information.
If you find you have an issue with call tampering, be sure to alert your service provider.
You should also invest in end-to-end encryption of your calls and look into introducing authentication codes into your calls.
If this is a recurring problem, you can also plan to become less reliant on voice calls for business. Consider sending customer updates as an example. For non-urgent information or updates, try using a
business SMS system. This will send customers all of the information that they need without the potential for noisy, inaudible calls while the issue is sorted.
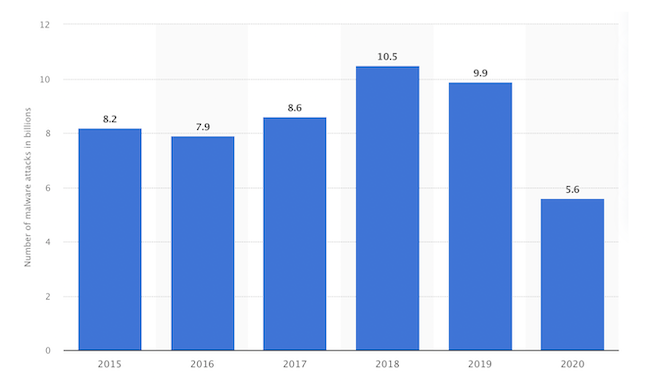
2. Malware
Malware and viruses are programs or pieces of data that can be introduced into your system and lead to weaknesses. They can also create opportunities for larger data leaks or hacks later on.
Source
As they relate to VoIP systems, malware and viruses can take up bandwidth and create delays and poor quality in a business phone system. This can be a particular issue for
small business VoIP systems that may not have the resources to constantly monitor for attacks.
However, there are ways that you can protect yourself against malware and viruses. You should ensure that you regularly scan your network for infection.
In addition, when migrating from one system to another, say when using a software development tool, (example from
Jira to ZenTao) it should be a secure migration process to avoid leaks and corruption of data. Similarly, if you are about to change your VoIP system to a cloud-based system, make sure that it is equipped with adequate security functions to avoid viruses and malware being able to access business and client information.
One of the best ways to protect against malware and viruses is to invest in anti-virus and virus detection software. These will monitor incoming information to make sure that it's secure before it's allowed into the system.
3. DDoS attacks
Distributed dDenial of sService (DDoS) attacks are cyber attacks where hackers stop businesses from being able to use their own VoIP services. They do this by flooding the servers with more data and requests than they can handle at any one time, making it impossible for the service to process data.
Signs of a DDoS attack include slow responses and long, unexpected bandwidth spikes. To mitigate the risks of DDoS attacks, you should consider using a dedicated internet connection specifically for your VoIP. One of the most effective for this purpose is a Vvirtual lLocal aArea nNetwork (VLAN) because it's easy to identify unusual data inputs which may be this type of attack.
4. Vishing
Vishing is a compound term for VoIP-based phishing. If you're unfamiliar with phishing, it's the name for a commonly used hacking method whereby cyber criminals pretend to be calling from a trusted number/organization in order to obtain personal information.
A common variation of phishing is a caller pretending to be affiliated with a bank in order to get bank information out of the call recipient.

Source
As you can imagine, vishing can be very bad news for consumer trust in a company. You'll need to
understand customer empathy journeys to understand why this is.
Imagine you're leading a marketing firm and one of your clients falls victim to a phishing attack by an individual pretending to be with your team. This is clearly not your business' fault, but, by empathizing with the client, you can see that they will have trouble trusting all future VoIP communications with you.
It's difficult to get around vishing attacks, although there are a few steps that you can take to prevent being targeted or falling victim to one:
Know which government organizations are commonly used in phishing. Always be skeptical of government calls asking for sensitive information, as they usually do not even initiate contact. Join the Do Not Call register.
If you find you have fallen victim to a successful or attempted vishing attack, make sure to keep your customers informed if it affects them. Encourage them to be careful when they think they're speaking to your business.
5. VOMIT
Don't be put off by the strange name! VOMIT stands for 'vVoice oOver mMisconfigured iInternet tTelephones.'. This is the name for when potential hackers seek to extract conversations and data directly from current calls. This means that they can easily extract sensitive data like passwords and the location of the outgoing call origin.
For example, say that your team is focusing on an
upward communication initiative to improve employee satisfaction rates. Each team member has been assigned a time to speak with their supervisor over the new VoIP system regarding pay and potential support.
If someone were to hack into this call, they would have access to the employee and supervisor's names, locations, and the employee's pay and personal evaluation.

Source
This is an issue that you need to be aware of before implementing your VoIP system. The reason for this is that, to solve this issue, you should think about using a VoIP service provider that automatically uses end-to-end encryption for all calls.
This step should prevent hackers from being able to understand the call, even if they do manage to access it.
Questions for your service provider
Not all VoIP providers are created equal. These are some of the most important questions for you to ask your service provider to make sure that they're providing you with a secure service.
What are your encryption methods? What is your response time to a breach? What are your support hours and methods? What is your uptime? Are you regulation-compliant?
This is not an exhaustive list, but positive answers to these questions is a sign that your service provider values security and data preservation.
Making your calls secure
VoIP systems come with potential security risks, the same as any other communication system. Because they are hosted on external servers, most of these security risks come from outside interference and data loss.
By understanding these potential risks, you can keep an eye out for them and manage them when they come up. In doing so, you can maintain your customer relationships, build trust, and
keep your business growing.
Opinions expressed by the author are not necessarily those of WITI.
Are you interested in boosting your career, personal development, networking, and giving back? If so, WITI is the place for you! Become a WITI Member and receive exclusive access to attend our WITI members-only events, webinars, online coaching circles, find mentorship opportunities (become a mentor; find a mentor), and more!
Founded in 1989, WITI (Women in Technology International) is committed to empowering innovators, inspiring future generations and building inclusive cultures, worldwide. WITI is redefining the way women and men collaborate to drive innovation and business growth and is helping corporate partners create and foster gender inclusive cultures. A leading authority of women in technology and business, WITI has been advocating and recognizing women's contributions in the industry for more than 30 years.






Comments